Cybersecurity Risk Management
Cybersecurity is quickly becoming one of the top priorities for numerous industries in recent years and maybe none bigger than the power and utilities industry. For example in the utilities industry, a malicious cybersecurity attack could have serious consequences; not only for the utility being attacked, but for the public that relies on their services. Billions of dollars would be at risk if major disruptions impacted the power, water, transportation, communications, small businesses, and other secure infrastructure and critical cyber assets. If a malicious cyber attacker gets access to a power or utility company, they can turn off or re-route services, shut off power, block 911 calls, reverse the flow of utility pumps, or steal consumer data and billing information. Ultimately, the utility industry itself has inherent cyber risks that constantly need to monitored and addressed.
Cybersecurity risk, as with all risks, cannot be completely eliminated, but instead must be managed through informed decision making practices. Cybersecurity Risk Management Processes are built on the principles that managing cybersecurity risk is critical to the success of an organization’s mission to achieve their business goals and objectives. Implementing a successful cybersecurity risk program will facilitate better informed decision making throughout an organization, which leads to more effective risk identification, resource allocation, operational efficiencies, and risk mitigation. The goal is to reduce the likelihood and impact of a cyber event occurring that may negative effect the organization.
To completely establish your cybersecurity framework, the following needs to be considered:
- Regulatory compliance requirements
- Maturity of your cybersecurity risk program
- Company Policies
- Company Goals and objectives
There are many different types of cybersecurity frameworks and each provide standards and guidelines to protect your organization against malicious cyber attacks. This has resulted in many industries establishing their own set of cybersecurity compliance requirements and standards. For example, the energy sector has the NERC CIP standards and the medical industry has HIPAA. To meet the standards, organizations can adopt guidance for cybersecurity risk from established publications such as the following:
- U.S. Department of Commerce, National Institute of Standards and Technology (NIST)
- U.S. Department of Energy, Cybersecurity Capability Maturity Model (C2M2)
- U.S. Department of Defense, Cybersecurity Maturity Model Certification (CMMC)
- Center for Internet Security, Inc. 20 Critical Security Control (CIS)
- International Organizations for Standardization and International Electrtechnical Organization, ISO/IEC 27001
- North American Electric Reliability Corporation (NERC), Critical Infrastructure Protection Standards (CIP)
It’s important to fully understand the framework of the security environment, to understand normal behavior and deviant behavior, and to have an expert set of eyes on the system at all times. A successful cybersecurity risk program, such as ARETE’s Risk Assessment Profiler (RAP), will result in an improved dialogue with actions to proactively manage risks instead of a reactive risk management approach.
Using RAP for Cybersecurity Risk Management
The RAP platform provides the ability to leverage an innovative platform with standard risk processes that can be used by individual business functions such as cybersecurity, capital projects, assets, enterprise, and more. RAP’s cybersecurity platform is designed to identify the risk gaps of your cybersecurity program compared to industry and compliance requirements needing to be adhered to. Being a template based risk management systems, RAP leverages the core cybersecurity frameworks such as NIST, C2M2, and CMMC and other standards.
NIST’s Risk Management Framework (RMF) is often the preferred go-to standard to a robust cybersecurity risk program due to its objectivity and fairness. It’s results-driven, giving organizations the flexibility when it comes to implementing risk practices. The NIST RMF has simple language, allowing people that are not cybersecurity experts to understand and use it. There are seven steps in NIST’s RMF which includes a preparatory step to ensure that organizations are ready to execute the process. All seven steps are essential for the successful implementation of Cybersecurity Risk Management (CRM) program. The following identifies the RMF steps supported with a brief description on how RAP can be leveraged by your organization to accomplish a successful CRM. For additional information visit the NIST Learning Page: Uses and Benefits of the Framework.
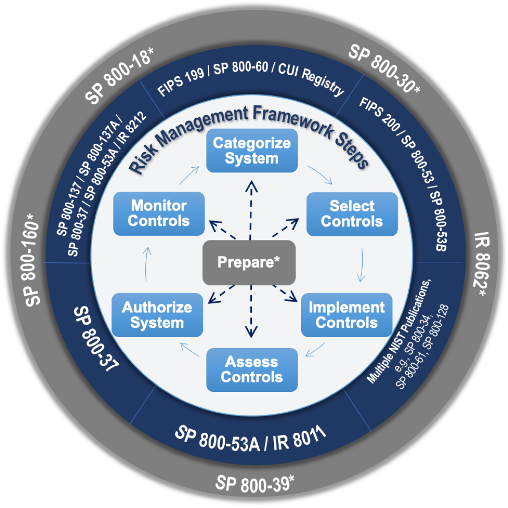
How RAP Accomplishes the 7 Steps of NIST’s Risk Management Framework
1. PREPARE to execute the RMF from an organization and a system-level perspective by establishing context and priorities for managing cybersecurity and privacy risk.
- RAP provides tools to prepare the platform’s framework by configuring the organization with divisions, departments, and regions.
- Users can have set roles, responsibilities and access to specific enterprise, agency, and department cyber program risk information.
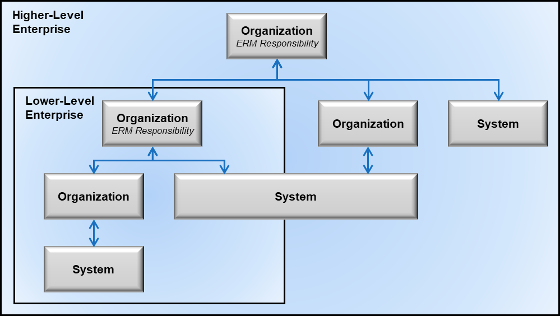
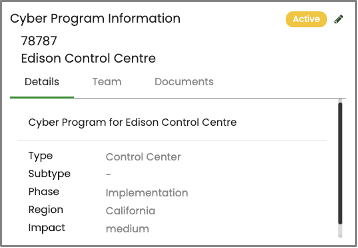
2. CATEGORIZE the templates data so that it will be processed, stored, and transmitted by the system based on an impact analysis.
- RAP provides the ability to categorize cyber system programs by impact level (low, medium, high) to process assessments and perform analysis.
- Cyber Programs will be identified for each part of the organization and access will be limited to those granted the appropriate permissions.
- If necessary, ARETE can load data for a series of cyber programs via excel import methods.
3. SELECT the baseline controls for the system and tailor them as needed to configure the acceptable risk levels.
- RAP provides the ability to configure the standard cybersecurity risk templates to obtain the appropriate risk levels from each assessment performed.
- Implement value-based risk element modeling for qualitative risk analysis to score risks in your cyber programs.
- Risk assessments will calculate risk scoring based on the risk template, which allows for risk ranking and prioritization.
- RAP’s maturity templates provide the ability to set control target levels at each risk element and Maturity Indicator Levels (MIL).
RAP NIST Cybersecurity Assessment Creation
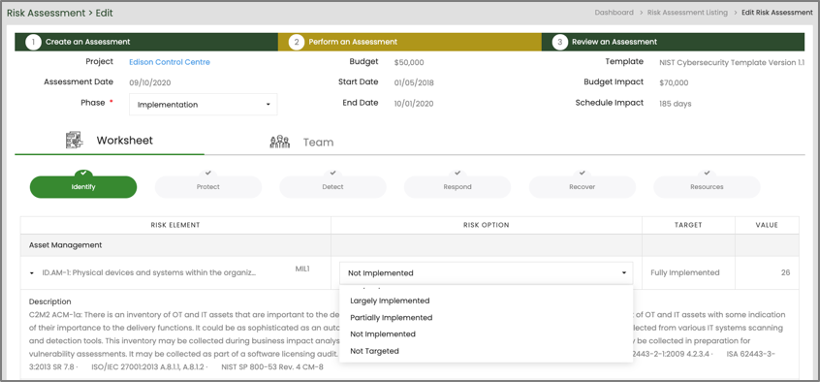
4. IMPLEMENT the controls and describe how the controls are employed within the system and its environment of operation.
- With each assessment completed, RAP provides a Cyber Program Dashboard that illustrates what controls have met their established target and maturity levels and which ones have not.
- Monitor the number of accomplished domain targets and the domains requiring mitigation.
RAP Cyber Domain Widget
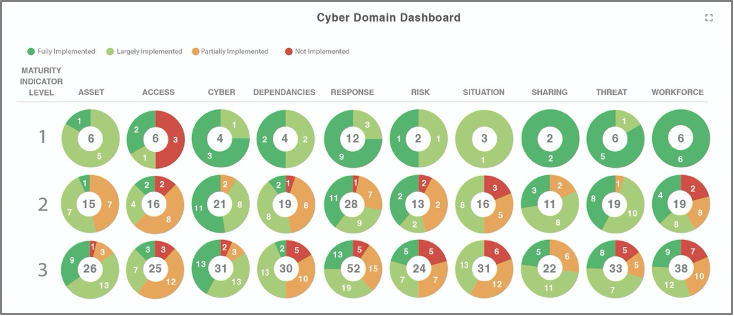
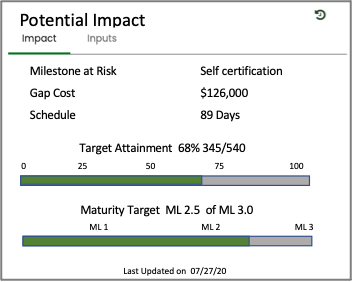
5. ASSESS the controls to determine if the controls are implemented correctly, operating as intended, and producing the desired outcomes with respect to satisfying the security and privacy requirements.
- RAP identifies the impact of the cyber program’s maturity and target attainments with associated impacts.
- Define milestones for each cyber program with associated cost and schedule. Milestones can consist of upcoming audits, self-certifications, compliance directives, etc.
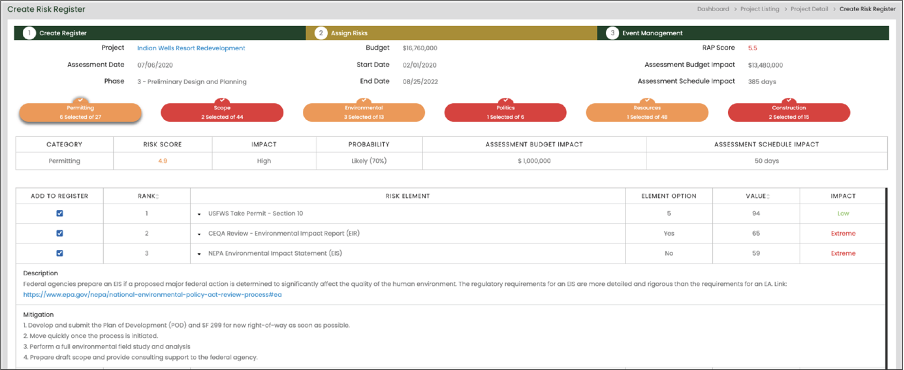
6. AUTHORIZE the system or common controls based on a determination that the risk to organizational operations and assets, individuals, other organizations, and the Nation is acceptable.
- Automatically create a risk register for each cyber program from identified risk categories, risk elements, and pre-configured mitigation considerations established by state guidelines.
- Identify risk events and take action by administering mitigation actions.
- Assign and collaborate on risk events with team participants.
- Continuously synchronize with new risk assessments performed throughout the life of the cyber program.
RAP Risk Register Creation
7. MONITOR the system and the associated controls on an ongoing basis to include assessing control effectiveness, documenting changes to the system and environment of operation, conducting risk assessments and impact analyses, and reporting the security and privacy posture of the system.
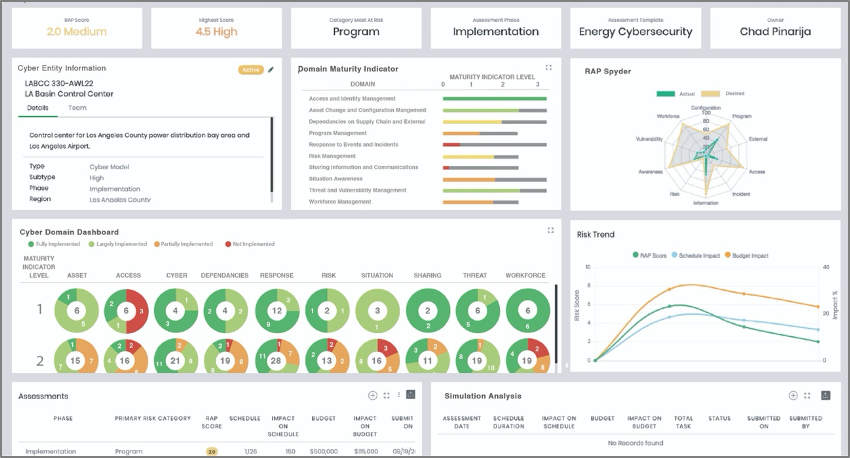
- RAP provides intuitive dashboards allowing users to review the cyber risk program portfolio data across the organization or filtered to one department and/or region.
- Assess the risk behavior throughout the life of the cyber program.
- Make better informed decisions by leveraging the widgets that provide insightful information and flags top risks.
- Generate risk reports and export cyber program data to excel for further analysis.
- Review and compare the cyber programs by qualitative RAP score, as known as risk exposure score. Below is a sample of the RAP Cyber Program dashboard.
RAP Cyber Program Dashboard
Make These Top Cybersecurity Standards and Guidelines Work For You!
The RAP platform supports many cyber risk frameworks, some of which are mentioned above. Using RAP to assess your organization will allow you to identify weak points. With that knowledge, your team will be able to address vulnerabilities by implementing the appropriate controls. RAP makes it easy to pinpoint your cyber risk management gaps and roadmap towards your target. Our risk register and milestone feature tracks progress and improvement, while our target profile feature allows for goal setting across the organization. RAP is the perfect solution to bridge the gap and accomplish your cybersecurity risk management goals!
Contact the ARETE team at (888) 99-ARETE or info@arete-inc.com to learn more and see RAP’s cybersecurity risk management platform in action!